The importance of web application security cannot be overstated, especially in a city like Chicago, where technology and innovation are thriving. As a hub for businesses, startups, and organizations, Chicago's online presence is vast and diverse. However, this also makes it a prime target for cyber threats and attacks. Web application penetration testing, also known as pen testing or ethical hacking, is a crucial process that helps identify vulnerabilities and weaknesses in web applications, allowing organizations to strengthen their security posture and protect their sensitive data.
In today's digital landscape, web applications are a crucial part of any organization's online presence. From e-commerce platforms to social media, web applications are used to interact with customers, process transactions, and store sensitive data. However, with the rise of web applications comes the increased risk of cyber threats and attacks. According to a recent report, web application vulnerabilities account for over 30% of all data breaches.

What is Web Application Pen Testing?
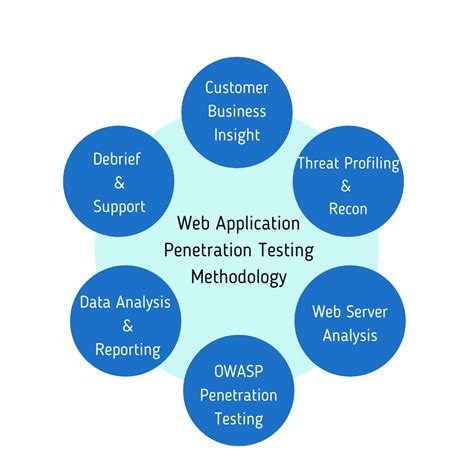
Web application penetration testing is a simulated cyber attack against a web application to test its defenses and identify potential vulnerabilities. The process involves a team of experienced security experts, known as penetration testers or ethical hackers, who use various techniques and tools to attempt to breach the web application's security controls.
The primary goal of web application pen testing is to identify vulnerabilities and weaknesses that could be exploited by malicious actors. By doing so, organizations can take proactive measures to patch vulnerabilities, strengthen their security controls, and prevent potential data breaches.
Benefits of Web Application Pen Testing
Web application penetration testing offers numerous benefits to organizations, including:
- Improved security posture: Web application pen testing helps identify vulnerabilities and weaknesses, allowing organizations to strengthen their security controls and reduce the risk of cyber attacks.
- Compliance with regulations: Many regulatory bodies, such as the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA), require web application pen testing as part of their security requirements.
- Cost savings: By identifying and patching vulnerabilities, organizations can avoid costly data breaches and reputational damage.
- Enhanced customer trust: Web application pen testing demonstrates an organization's commitment to security and customer data protection, enhancing customer trust and loyalty.
Top Security Checks for Web Application Pen Testing
When it comes to web application pen testing, there are several security checks that should be performed to ensure the integrity and security of the application. Some of the top security checks include:
- Input validation: Verifying that user input is validated and sanitized to prevent SQL injection and cross-site scripting (XSS) attacks.
- Authentication and authorization: Testing the application's authentication and authorization mechanisms to ensure that only authorized users can access sensitive data and functionality.
- Session management: Verifying that session management is properly implemented to prevent session hijacking and other attacks.
- Error handling: Testing the application's error handling mechanisms to ensure that sensitive data is not disclosed in error messages.
- Secure coding practices: Reviewing the application's source code to ensure that secure coding practices are followed, such as secure data storage and transmission.

Web Application Pen Testing Tools
There are several web application pen testing tools available, including:
- Burp Suite: A popular web application security testing tool that includes a range of features, such as proxying, scanning, and intrusion testing.
- OWASP ZAP: An open-source web application security scanner that can be used to identify vulnerabilities and weaknesses.
- SQLMap: A tool that is specifically designed to identify and exploit SQL injection vulnerabilities.

Web Application Pen Testing in Chicago
Chicago is a hub for businesses and organizations, and as such, web application pen testing is a crucial process that can help protect sensitive data and prevent cyber attacks. There are several web application pen testing companies in Chicago that offer a range of services, including:
- Web application security testing: Identifying vulnerabilities and weaknesses in web applications.
- Penetration testing: Simulated cyber attacks against web applications to test their defenses.
- Vulnerability assessment: Identifying and prioritizing vulnerabilities in web applications.

Conclusion
Web application pen testing is a crucial process that can help protect sensitive data and prevent cyber attacks. By identifying vulnerabilities and weaknesses, organizations can take proactive measures to strengthen their security controls and reduce the risk of data breaches. If you're looking for web application pen testing services in Chicago, there are several companies that offer a range of services, including web application security testing, penetration testing, and vulnerability assessment.
Gallery of Web Application Pen Testing






FAQ
What is web application pen testing?
+Web application penetration testing is a simulated cyber attack against a web application to test its defenses and identify potential vulnerabilities.
Why is web application pen testing important?
+Web application pen testing helps identify vulnerabilities and weaknesses, allowing organizations to strengthen their security controls and reduce the risk of cyber attacks.
What are the benefits of web application pen testing?
+The benefits of web application pen testing include improved security posture, compliance with regulations, cost savings, and enhanced customer trust.