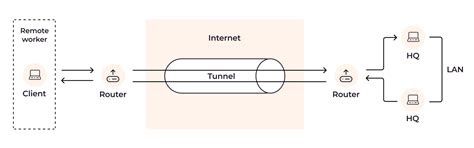
In the world of networking and cybersecurity, tunneling is a crucial concept that enables secure and private communication over the internet. One type of tunneling is application tunneling, which allows applications to communicate with each other securely and efficiently. In this article, we will delve into the world of application tunneling, exploring its definition, benefits, and working mechanisms.
What is Application Tunneling?
Application tunneling is a technique that enables applications to communicate with each other over a network, such as the internet, in a secure and private manner. It involves encapsulating application data within another protocol, such as TCP/IP, to create a secure "tunnel" between the applications. This tunneling process allows applications to communicate with each other without exposing their data to the public internet.

How Does Application Tunneling Work?
Application tunneling works by using a combination of protocols and techniques to create a secure tunnel between applications. Here's a step-by-step explanation of the process:
- Establishing a Connection: The application initiates a connection to a tunneling server or a peer application.
- Authentication and Authorization: The application authenticates and authorizes the connection using various methods, such as username/password, certificates, or tokens.
- Encapsulation: The application data is encapsulated within another protocol, such as TCP/IP, to create a secure tunnel.
- Tunneling: The encapsulated data is transmitted over the network, such as the internet, to the tunneling server or peer application.
- Decapsulation: The tunneling server or peer application receives the encapsulated data and decapsulates it, extracting the original application data.
- Delivery: The extracted application data is delivered to the intended recipient application.
Benefits of Application Tunneling
Application tunneling offers several benefits, including:
- Security: Application tunneling provides end-to-end encryption, ensuring that data remains confidential and secure.
- Privacy: Tunneling helps protect user data from interception and eavesdropping.
- Flexibility: Application tunneling allows applications to communicate with each other over different networks and protocols.
- Scalability: Tunneling enables applications to scale more efficiently, as it reduces the need for multiple connections and protocols.
Types of Application Tunneling
There are several types of application tunneling, including:
- SSH Tunneling: Uses Secure Shell (SSH) protocol to create a secure tunnel between applications.
- SSL/TLS Tunneling: Uses Secure Sockets Layer/Transport Layer Security (SSL/TLS) protocol to create a secure tunnel between applications.
- IPSec Tunneling: Uses Internet Protocol Security (IPSec) protocol to create a secure tunnel between applications.
Real-World Examples of Application Tunneling
Application tunneling is used in various real-world scenarios, including:
- Remote Access: Application tunneling enables remote access to applications and resources over the internet.
- Cloud Computing: Tunneling enables secure communication between applications and cloud services.
- IoT: Application tunneling enables secure communication between IoT devices and applications.
Gallery of Application Tunneling






FAQs
What is application tunneling?
+Application tunneling is a technique that enables applications to communicate with each other securely and efficiently over a network.
How does application tunneling work?
+Application tunneling works by encapsulating application data within another protocol, such as TCP/IP, to create a secure tunnel between applications.
What are the benefits of application tunneling?
+Application tunneling provides security, privacy, flexibility, and scalability benefits.
In conclusion, application tunneling is a powerful technique that enables secure and efficient communication between applications over a network. By understanding how application tunneling works and its benefits, organizations can leverage this technology to improve their security posture and enable more efficient communication between applications.