The digital age has brought with it a plethora of benefits, but also a host of security concerns. As technology advances, so too do the methods of cybercriminals, making it increasingly important for organizations to prioritize data security. One of the most effective ways to secure data is through application-level encryption.

In this article, we'll explore five ways to secure data with application-level encryption, providing you with the knowledge you need to protect your organization's sensitive information.
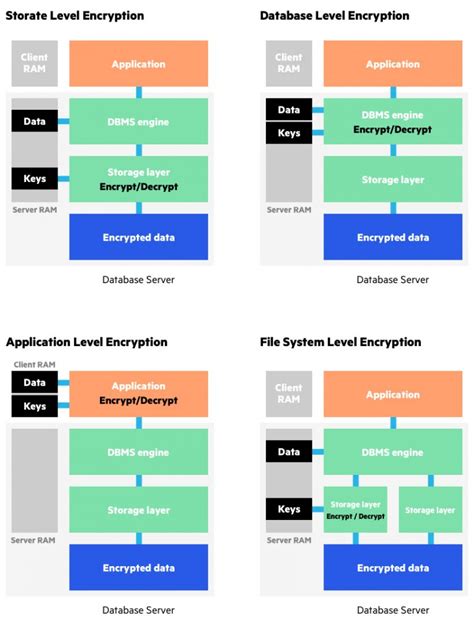
What is Application-Level Encryption?
Before we dive into the ways to secure data with application-level encryption, let's first define what it is. Application-level encryption is a method of encrypting data within an application, rather than relying on encryption at the network or storage level. This approach provides an additional layer of security, ensuring that even if data is intercepted or accessed unauthorized, it will be unreadable without the decryption key.
1. Data at Rest Encryption
One of the most common use cases for application-level encryption is data at rest encryption. This involves encrypting data that is stored within an application, such as customer information or financial data. By encrypting data at rest, organizations can prevent unauthorized access, even in the event of a data breach.

To implement data at rest encryption, organizations can use a variety of encryption algorithms, such as AES or PGP. These algorithms ensure that data is scrambled and unreadable, even to authorized personnel, without the decryption key.
Benefits of Data at Rest Encryption
- Prevents unauthorized access to sensitive data
- Meets regulatory requirements for data security
- Provides an additional layer of security in the event of a data breach
2. Data in Motion Encryption
In addition to data at rest encryption, application-level encryption can also be used to secure data in motion. This involves encrypting data as it is transmitted between applications or systems, preventing interception and unauthorized access.

To implement data in motion encryption, organizations can use protocols such as SSL/TLS or HTTPS. These protocols ensure that data is encrypted as it is transmitted, preventing interception and unauthorized access.
Benefits of Data in Motion Encryption
- Prevents interception and unauthorized access to sensitive data
- Meets regulatory requirements for data security
- Provides an additional layer of security for data transmitted between applications or systems
3. Key Management
Effective key management is critical to the success of application-level encryption. This involves managing the creation, distribution, and storage of encryption keys, ensuring that they are secure and accessible only to authorized personnel.

To implement effective key management, organizations can use a variety of techniques, such as key wrapping and key rotation. These techniques ensure that encryption keys are secure and accessible only to authorized personnel.
Benefits of Effective Key Management
- Ensures the security and integrity of encryption keys
- Prevents unauthorized access to sensitive data
- Meets regulatory requirements for key management
4. Tokenization
Tokenization is a technique used to replace sensitive data with a non-sensitive equivalent, known as a token. This approach can be used to secure data within an application, preventing unauthorized access and reducing the risk of data breaches.

To implement tokenization, organizations can use a variety of techniques, such as data tokenization and format-preserving tokenization. These techniques ensure that sensitive data is replaced with a non-sensitive equivalent, preventing unauthorized access.
Benefits of Tokenization
- Prevents unauthorized access to sensitive data
- Reduces the risk of data breaches
- Meets regulatory requirements for data security
5. Format-Preserving Encryption
Format-preserving encryption is a technique used to encrypt data in a way that preserves its original format. This approach can be used to secure data within an application, preventing unauthorized access and reducing the risk of data breaches.

To implement format-preserving encryption, organizations can use a variety of techniques, such as FF1 and FF3-1. These techniques ensure that data is encrypted in a way that preserves its original format, preventing unauthorized access.
Benefits of Format-Preserving Encryption
- Prevents unauthorized access to sensitive data
- Preserves the original format of data
- Meets regulatory requirements for data security






In conclusion, application-level encryption is a critical component of any data security strategy. By implementing the five techniques outlined above, organizations can ensure the security and integrity of their sensitive data, reducing the risk of data breaches and meeting regulatory requirements.
If you have any questions or comments about this article, please don't hesitate to reach out. We'd love to hear from you!
What is application-level encryption?
+Application-level encryption is a method of encrypting data within an application, rather than relying on encryption at the network or storage level.
What are the benefits of application-level encryption?
+The benefits of application-level encryption include preventing unauthorized access to sensitive data, meeting regulatory requirements for data security, and providing an additional layer of security in the event of a data breach.
How does tokenization work?
+Tokenization is a technique used to replace sensitive data with a non-sensitive equivalent, known as a token. This approach can be used to secure data within an application, preventing unauthorized access and reducing the risk of data breaches.