In today's digital age, protecting sensitive data is more crucial than ever. With the increasing number of cyber attacks and data breaches, it's essential to take proactive measures to safeguard your data. One effective way to do this is by using application encryption. In this article, we'll delve into the world of application encryption, exploring its importance, benefits, and best practices.
What is Application Encryption?
Application encryption is the process of converting plaintext data into unreadable ciphertext to prevent unauthorized access. This is achieved through the use of encryption algorithms and keys, which scramble the data, making it inaccessible to anyone without the decryption key. Application encryption can be applied to various types of data, including sensitive information, confidential communications, and even entire applications.
Why is Application Encryption Important?
In today's digital landscape, data breaches and cyber attacks are becoming increasingly common. According to a report by Cybersecurity Ventures, the global cost of cybercrime is expected to reach $6 trillion by 2025. Application encryption is a critical component of a robust cybersecurity strategy, providing an additional layer of protection against unauthorized access and data breaches.

Benefits of Application Encryption
Application encryption offers numerous benefits, including:
- Data Protection: Application encryption ensures that sensitive data is protected from unauthorized access, even in the event of a data breach.
- Compliance: Application encryption helps organizations comply with regulatory requirements, such as GDPR, HIPAA, and PCI-DSS.
- Trust: Application encryption demonstrates a commitment to data security, fostering trust among customers, partners, and stakeholders.
- Competitive Advantage: Organizations that prioritize application encryption can differentiate themselves from competitors and establish a reputation for data security.
How Does Application Encryption Work?
Application encryption involves several steps:
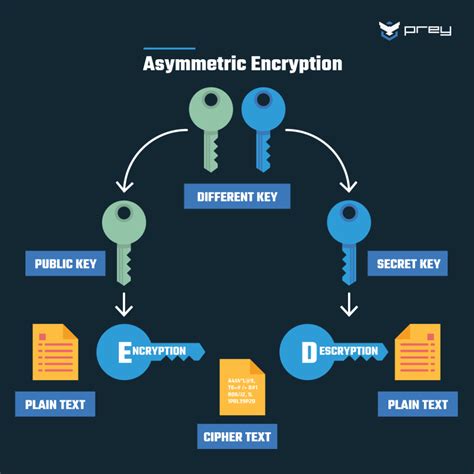
- Key Generation: A pair of keys is generated, consisting of a public key and a private key.
- Data Encryption: The public key is used to encrypt the data, converting it into unreadable ciphertext.
- Data Storage: The encrypted data is stored securely, often in a encrypted database or file system.
- Data Decryption: The private key is used to decrypt the data, converting it back into plaintext.
Types of Application Encryption
There are several types of application encryption, including:
- Symmetric Encryption: Uses the same key for encryption and decryption.
- Asymmetric Encryption: Uses a pair of keys, with the public key used for encryption and the private key used for decryption.
- Hash Functions: Uses a one-way encryption algorithm to create a fixed-size string of characters.
Best Practices for Application Encryption
To ensure effective application encryption, follow these best practices:
- Use Strong Keys: Use large, randomly generated keys to prevent brute-force attacks.
- Choose the Right Algorithm: Select an encryption algorithm that is widely accepted and regularly reviewed.
- Implement Secure Key Management: Use a secure key management system to store, manage, and rotate keys.
- Regularly Update and Patch: Regularly update and patch encryption software to prevent vulnerabilities.
Common Challenges and Solutions
While application encryption is a powerful tool, it's not without its challenges. Here are some common challenges and solutions:
- Key Management: Use a secure key management system to store, manage, and rotate keys.
- Performance: Use efficient encryption algorithms and optimize encryption processes to minimize performance impact.
- Interoperability: Use standardized encryption protocols to ensure seamless communication between systems.
Conclusion
Application encryption is a critical component of a robust cybersecurity strategy. By understanding the importance, benefits, and best practices of application encryption, organizations can protect sensitive data and prevent cyber attacks. Remember to choose the right algorithm, implement secure key management, and regularly update and patch encryption software to ensure effective application encryption.





FAQ
What is application encryption?
+Application encryption is the process of converting plaintext data into unreadable ciphertext to prevent unauthorized access.
Why is application encryption important?
+Application encryption is important because it provides an additional layer of protection against unauthorized access and data breaches.
What are the benefits of application encryption?
+The benefits of application encryption include data protection, compliance, trust, and competitive advantage.